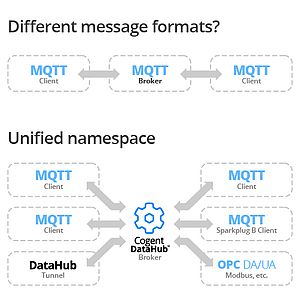
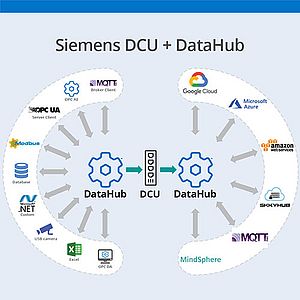
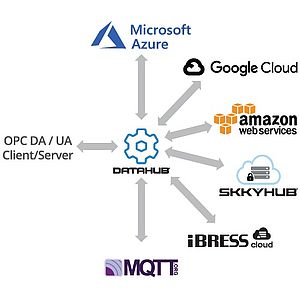
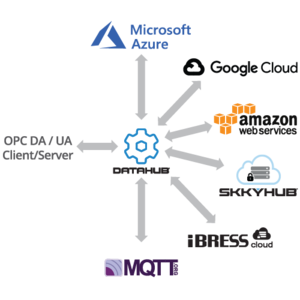
Today’s competitive realities are forcing enterprises to access data from industrial operations. Industry 4.0 and Industrial IoT demand that companies pull real-time or historical data from production and feed it to IT departments at head office or in the cloud. The question has become: How to do that securely?
DMZs: essential for OT/IT cybersecurity
Industrial security experts and governmental agencies agree that the most secure way to connect OT and IT is to segregate networks by using a DMZ (“demilitarized zone”). The NIS 2 Directive from the European Commission encourages DMZs to ensure separation between corporate networks and control networks, and allow only known and authenticated users. A NIST SP-800-82 document describes the value and use of firewalls to separate these zones, and to ensure that only the correct data passes from one to the other.
The challenge: passing data over a DMZ
Most industrial data communication technologies were not designed for accessing plant data through a DMZ. Such a connection requires two or more servers chained together one after the other. The most widely-used industrial protocols are either too complex to reproduce well in a daisy chain like this, or they cannot reliably pass data quality information from one end to the other, making data at the end of the chain unreliable.
The solution: DMZ-compatible tunnelling
Some secure tunnelling implementations support daisy-chained servers across a DMZ because they mirrors the full data set at each node. They provide access to the data at each link of the chain, and can guarantee consistency of the data, so that any client or intermediate point maintains the same values as the original source.
You should not have to choose between data access and security. The right tunnelling technology can connect OT and IT systems securely for one-way or bidirectional data flow in real time. It is possible to achieve a level of security comparable to an in-plant network, and still allow access the production data you need.