Following risk analysis, Volkswagen AG has introduced a new security standard for its car bodywork production network at its plant in Emden, Germany. Thanks to the segmentation of the network, the installation of industrial firewalls, and stricter access rules, the systems are now protected against unauthorized access.
Ethernet-based production systems are becoming increasingly well-established. Easy integration into Intranet and Internet, the high bandwidth of up to Gigabits per second and decreasing costs of industrially specified cables, connectors, switches, and routers are the reasons behind this development. The other side of the coin is an increased risk of malfunctions and production interruptions due to security loopholes in industrial networks. For this reason, an internal risk analysis was conducted at Volkswagen AG's Emden car body production plant and the security of the systems was scrutinized, including their control technology. The result: sensitive production systems were insufficiently protected against unauthorized access because attacks can be triggered by malware, inadvertent access or unintentional misentries during internal network operations and their prevention by centralized firewalls is very complex and not cost-effective.
Employees of third party companies, who access the network using their laptops during service operations or for hardware and software installations can unintentionally spread malware, and are deemed to pose a potential risk. Unintentional misentries were also identified as problematic weaknesses. Jens Hoofdmann, Bodywork Maintenance Specialist, cites one problematic issue arising from the analysis: "a typical example is the installation of a server which subsequently sends ping packets to the entire network at short intervals. Such permanent requests can disrupt or even crash an industrial controller."
New security rules for the industrial network
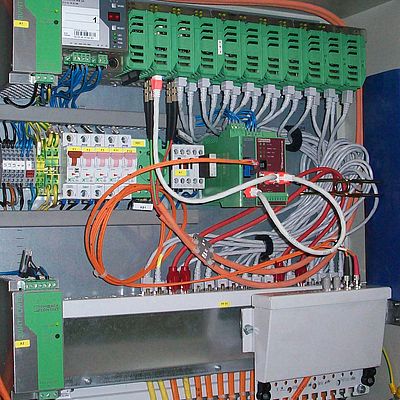
An action item matrix was developed based on the risk assessment, encompassing organizational changes, network segmentation, and the introduction of distributed industrial firewalls. When it came to selecting suitable hardening and security measures Volkswagen AG's Emden plant opted for industrial routers with an integrated firewall. The distributed industrial firewall/router solution segments the production network in the car body construction plant at Emden into 15 isolated subnetworks. For central protection featuring comparable granularity all systems and sub-networks would need star layout network cabling with a high-capacity firewall in a complex configuration. Given the typical distances between network nodes at industrial plants this proves particularly expensive and inefficient which is why these environments are virtually dominated by tree-shaped and linear cable topologies and therefore better suited to a distributed firewall approach.
Distributed industrial firewall/router solution
The central IT department was also involved in the preliminary discussions regarding implementing the new structure, the technical evaluation, and startup monitoring. The production-related IT department ultimately assumed responsibility for addressing the planning, installation, commissioning, and administration tasks.
The system network had already been successfully planned and put into operation in conjunction with the German automation specialist Phoenix Contact. The positive experience gained from this project and the knowledge acquired of the systems also proved highly beneficial during the network protection operations. The company put its trust in FL mGuard industrial firewall/router modules from Phoenix Contact and Innominate. The key criteria in their selection were their suitability for industrial applications and the availability of a central management system.
The mGuard modules are based on a robust embedded Linux and integrate four perfectly coordinated security components: a bidirectional stateful inspection firewall, a flexible NAT router, a secure VPN gateway, and industry-suitable protection against malware as an option.
The fact that the mGuard security appliance is self-sufficient and can be subsequently integrated into existing production networks without repercussions using its stealth mode of operation proved to be particularly advantageous. As such, in routing terms the firewall behaves transparently as a bridge.
Setting up industrial firewalls
From Jens Hoofdmann's perspective, installing, setting up, and integrating the industrial firewalls was rather easy. The devices were used in a distributed manner in control cabinets for every uplink connection. In hardware terms, Volkswagen AG was able to mount the 24V DIN rail devices directly into the control cabinets and allow its own staff members to start them up based on the existing network structure and without any re-cabling operations.
Jens Hoofdmann explains that a very pragmatic approach was adopted towards setting up the firewall rules. In the first instance, all data traffic was permitted and access to the subnetworks was only logged. The log files were subsequently evaluated and recorded in the form of rules governing which type of access should be permitted in future. The rules were tested, revised, and finally defined in their present form.
During this phase, the company was able to utilize the experience of Innominate, a fully owned Phoenix Contact subsidiary. Jens Hoofdmann states: "we benefited extensively from Innominate's first-class expertise in industrial networks, protocols, and firewall rules and were thus able to optimize and enhance the structure of the installations".
A central management system
The Innominate Device Manager (IDM) central management system features a template mechanism facilitating central configuration and management of all mGuard devices. The parameters for firewall rules and NAT settings are directly configured in IDM without abstract security policies needing to be defined. The upload function is used to upload the rules to all the listed devices and configure them in one step. The IDM enabled special rules to be implemented between the subnetworks, subgroups, and user groups and then distributed to all firewalls.
According to the maintenance team at Volkswagen Emden, device management has been greatly facilitated by the central management system. Generating a new firewall rule within five minutes in order to grant a member of the service team access, for example, is no longer an issue.
Protection for sensitive production applications
Robots, PLCs, panel PCs, laser technology, welding systems, controllers, and the driverless transport system have since been protected by distributed firewalls on the Emden car bodywork production network. Jens Hoofdmann reports that there have been no security incidents since the firewalls were installed. However, they have been able to identify infected devices from other production sectors based on the log files. In one of these instances, a virus had attempted to spread to other devices. However, access to the protected computers was blocked and it was possible to advise the other sectors of the malicious malware. Jens Hoofdmann: "our experience with the mGuard industrial firewalls is nothing but positive. We are completely satisfied. The support provided by Innominate was also extremely professional as and when problems arose. All unauthorized access is blocked and the systems are now better protected against malware."