President and global CEO of Futurism Technologies, Sheetal Pansare is well known in the league of business leaders who are committed to bringing a total digital transformation in the businesses. For the last 15 years, he has delivered operational efficiency to businesses of various sizes and segments through Big Data, Data Analytics, Artificial Intelligence, Machine Learning, Mobility, Internet of Things (IoT), and Cloud Platforms. Currently heading the Futurism Technologies, which has a cross-continental presence in countries like India, the US, UK, Australia, and UAE, he is striving hard to visualize the new possibilities of digitizing the businesses.
Cyber threats, what were once considered to be a nuisance of big organizations, have now become a meandering menace. The estimations that cybercrime will cost the world $6 trillion by the end of 2020 is a standing testimony to the spreading tentacles of cyber threats. Small or big ventures, financial or automation sector, no segment is an exception to fly under its radar. In fact, with the enhancement in the sophistication of cybercrimes, the sphere of loss is not just limited to the loss of data. Coupled with the interconnected nature of modern systems and businesses, it can result in stolen money, vanished productivity, embezzlement of intellectual property, fraud, post-attack disturbance to the customary course of business, forensic examinations, and very apparent reputational harm.
Now put this inherently gloomy picture in the context of the statistical insight that there will be 3.5 million unfilled cybersecurity jobs in 2021. This all-too palpable shortage of experts will heighten the curve of threat, as it is rendering the business world virtually defenseless. The nonprofit Information Security Forum, considered to be a global authority on cyber risk management, notifies in its annual Threat Horizon report of the amplified potential of cyber threats for:
Disruption — Over-dependence on friable connectivity can heighten the risk of ransomware, which will be used in hijacking the Internet of Things.
Distortion — The deliberate spread of fabricated information via bots and automated sources can damage the integrity of sensitive information.
Deterioration — A combination of intelligent technologies and harsh demands generated by evolving national security and individual privacy regulations can adversely impact organizations’ capability to maintain the authenticity of their own information.
Clearly, the wisest thing that the business world can do now is to steadily increase its immunity against prevalent disasters by proactively peeping into the future of cyber threats. This article tries to help you in zeroing on the cyber threats that may be tailing 2021. Note that the threat is less threatening when it is aborted at its preliminary stage. And a prerequisite to that abortive action is the identification of the threat itself.
Here are the real cybersecurity threats that can prove disruptive in 2021.
1) System Piggybacking
System piggybacking infers that someone is accessing your system without your consent. In this threat, hackers usually break into defenseless networks and use the system as an instrument to conduct unlawful activities. The most common demonstration of piggybacking is attaining cryptocurrency via strategies like Bitcoin mining.
The best way to protect your system from piggybacking is to change your Wi-Fi password regularly to extended passwords with a complex mix of numbers, letters, and symbols. Note that if you are staying in a high traffic area, it is necessary for you to change your password more often. In the case of home network, you can switch off your wireless router and hard-wire all the essentials of your router. Hackers won’t be able to access your wireless network and piggyback if it’s off.
2) Deepfakes
A combination of the words "deep learning" and "fake", deepfakes are synthetic media in which a person in an existing image or video is substituted with someone else. Though the act of faking content is a not new, deepfakes utilize powerful techniques from machine learning and artificial intelligence to manipulate the content with even greater potential of misleading. The common machine learning methods deployed to create deepfakes are based on deep learning and include training generative neural network architectures like autoencoders or generative adversarial networks (GANs).
The only way to detect and negate deepfakes is to use algorithms analogous to the ones used to create them. By identifying patterns in the creations of deepfakes, the algorithm can pinpoint subtle inconsistencies. Experts have envisioned automatic systems that inspect videos for inaccuracies such as irregular blinking patterns of lighting. Few researchers have also advocated the use of Blockchain to authenticate the original source of the media. Videos can be verified through the ledger before they enter into the domain of social media. As a result, only videos from trusted and verified sources would be permitted, lessening the spread of enormously damaging deepfake media.
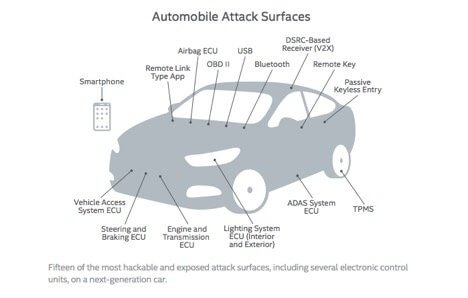
3) IoT Powered Connected Cars
The driver-less car might be away from us, but the connected car isn’t. According to a report titled “7 Connected Car Trends Fueling the Future”, almost 90 percent of new cars will be connected to the internet by the end of 2020. A connected car uses onboard sensors to optimize its operational efficiency and control. Usually, this is done by deploying embedded smartphone integration.
For hackers, this progression in automobile manufacturing and design opens up another prospect to exploit weaknesses in systems and siphoned away sensitive data. Along with safety concerns, connected cars pose severe threats to individual privacy.
4) Drones
We are observing the transmission of drones from specialty to commodity items. Citing the evil nature of cybercriminals, the easy access to drones will come with greater possibilities of threats and privacy intrusions. They may use Raspberry Pi computers and Wi-Fi sniffers to intervene and listen in on important and sensitive telecommunications. Credentials to access corporate networks, thus, may no longer remain a moving target for potential miscreants.
The successful drone attack against Saudi oil amenities in September 2019 has proved that the use of drones as a cyber-weapon is not unimaginable. It’s much more practical.
5) Cloud Jacking
When detractors of the cloud system say that it's not ready to handle wide-scale enterprise use, they usually underline security as a key concern. The simplest exploits include "cloud jacking" or "cloud hijacking". This happens when a deceitful entity takes control of your cloud infrastructure typically by using an automated exploit script. It's very common in the universe of botnets in which compromised computing resource is utilized to develop an exploit map of the cloud.
Looking at the massive rise in the use of Cloud systems, it’s not an act of great foresight to predict that Cloud Jacking will become a prominent cybersecurity threat in the coming times. The security strategists should keep in mind that one of the major 2019 breaches, the Capital One breach, happened when a hacker intruded on the servers of a third-party Cloud computing provider that Capital One was using. This unprecedented breach compromised the secrecy of 106 million records. Looking at the sharpening of the methods of hackers, there is a lot to believe that we will be witnessing more such attacks in 2021.
The Time to Prepare is Now
As technological advancements are evolving, so are cyber threats. This reality demands that organizations listen to the footsteps of time and create full-proof systems to deter cyberattacks. While you develop a strong firewall with external help, internal awareness is equally important. That’s precisely why the notion that maintaining cyber hygiene is an exclusive task of the IT department needs to go away. From board members to the nontechnical staff, active and vigilant participation of everyone is the only silver bullet that can keep you afloat in the whirlwind of modern cyber threats.
Moreover, considering the deep hole that cyberattacks can create in your pocket, cybersecurity literally puts you face to face with a binary situation: either be prepared or perish. And time for that preparation is now!
Sheetal Pansare